Azure landing zones
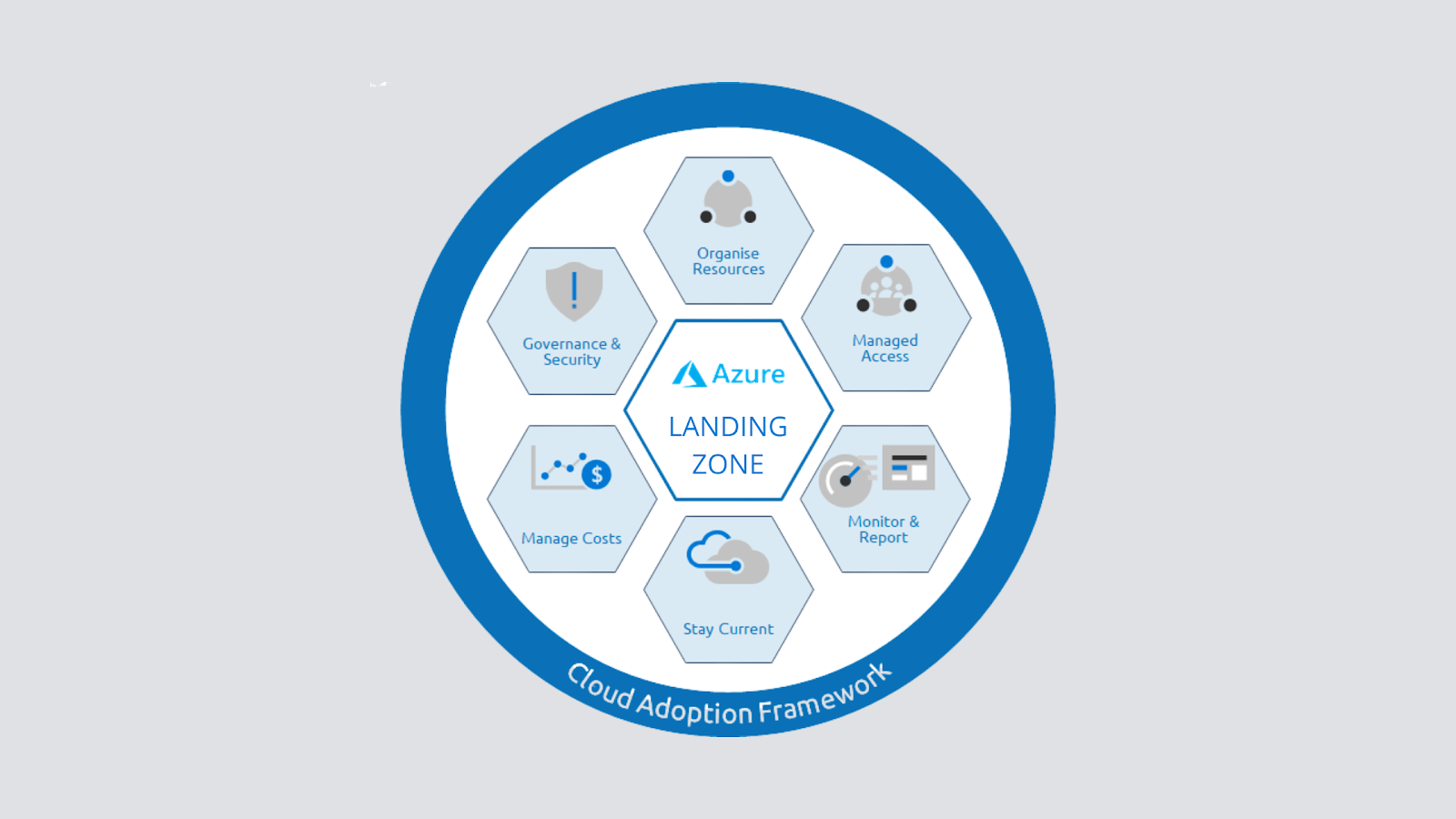
Azure landing zones are a vast topic that we could write a book on in terms of their design, implementation, and how they are assessed. In simple terms, an Azure landing zone talks about subscription democratization, where we have multiple subscriptions meant for different types of workloads. Following this architecture will help you build an architecture that is responsible for scalability, security, governance, compliance, networking, and identity. There are two types of landing zones: • Platform landing zones: A central team for several central teams is split by functions, such as networking, identity, and others. It will deploy subscriptions to deliver unified services. These subscriptions are used for various applications and workloads. Platform landing zones are usually used to consolidate certain essential services for better efficiency and ease of operations. Examples of these essential services include networking components (ExpressRoute, VPNs, firewalls, NVA, ...












