How to enable MFA in Azure AD
From an administrator's perspective, MFA activation in Azure AD is straightforward:
1. In the Azure portal, navigate to Azure Active Directory and select the Users navigation pane. In the upper navigation pane, select Per-user MFA, as shown in Figure 1.1:
Figure 1.1 – MFA activation in the Azure portal
2. You will be redirected to a retro-style portal at the windowsazure.com domain, in which you can enable or disable MFA for single users or bulk-update them by selecting several accounts or using a CSV file in the users tab.
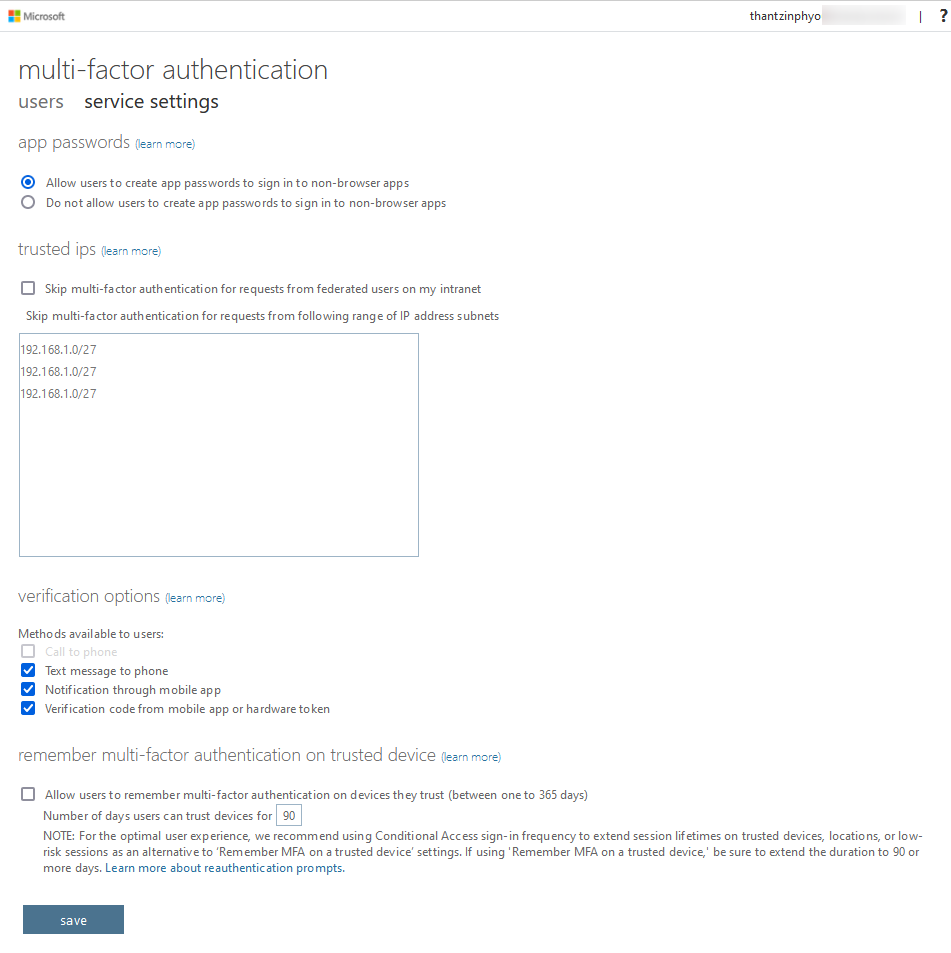
3. Before you enable MFA for all user accounts, first switch from the users tab to the service settings tab to configure some custom settings for your environment, as shown in Figure 1.2:
The first option is to allow or disallow users to create app passwords for legacy non-browser apps that do not support MFA. Outlook used to be such an application back in the days; however, nowadays, most applications should be able to authenticate with MFA.
You can also define trusted IPs for which you can skip MFA. So, for example, if your users are authenticating from one of your corporate offices and you have defined your external IP range(s) here, you can define that MFA challenges are only triggered when someone wants to authenticate from outside your corporate buildings. You can also enable and disable single verification options if they do
not fit your company's needs. The last setting is to allow users to remember MFA for devices they (but not you as a company!) trust. If you enable that option, users are not prompted with an MFA challenge again for a given period of time (between 1 and 365 days) on a particular device.
4. Now, back to enabling user accounts for MFA on the users tab. When you click the Enable link on the right side after selecting one or several user accounts (see Figure 1.3), you are prompted to read the online deployment guide and then click on enable multifactor auth. That's all from an administrator's point of view. Pretty easy? Indeed.
Figure 1.3 – Enabling MFA for one or several user accounts
The MFA-activated user has to configure all individual settings after the next login attempt. Telephone numbers for the account are taken from the information that is already stored in Azure AD. However, the user can update these numbers in the wizard that appears after the next logon.
Thant Zin Phyo@Cracky (MCT, MCE, MVP)


Comments
Post a Comment