Using Azure Virtual Desktop with Microsoft Intune
The following steps are not needed within Windows 365, as the enrolment into Intune happens automatically. Also, make sure that you have followed the previous step (setting MDM user scope to All and MAM user scope to None) before continuing.
Prerequisites:
• Running Windows 10 Enterprise, version 1809 or later, or running Windows 11.
• Set up personal remote desktops in Azure.
• Microsoft Entra hybrid joined and enrolled in Intune in one of the following methods:
• Configure Active Directory group policy to automatically enrol devices that are Microsoft Entra hybrid joined.
• Configuration Manager co-management.
• User self-enrollment via Microsoft Entra join.
• Microsoft Entra joined and enrolled in Intune by enabling Enroll the VM with Intune in the Azure portal.
Keep in mind that the following Windows 10 desktop device remote actions aren’t supported/recom- mended for Azure Virtual Desktop virtual machines:
• Autopilot reset
• BitLocker key rotation
• Fresh start
• Remote lock
• Reset password
• Wipe and Retire
Deleting VMs from Azure leaves orphaned device records in Intune. They’ll be automatically cleaned up if the built-in cleanup rules are configured for the tenant.
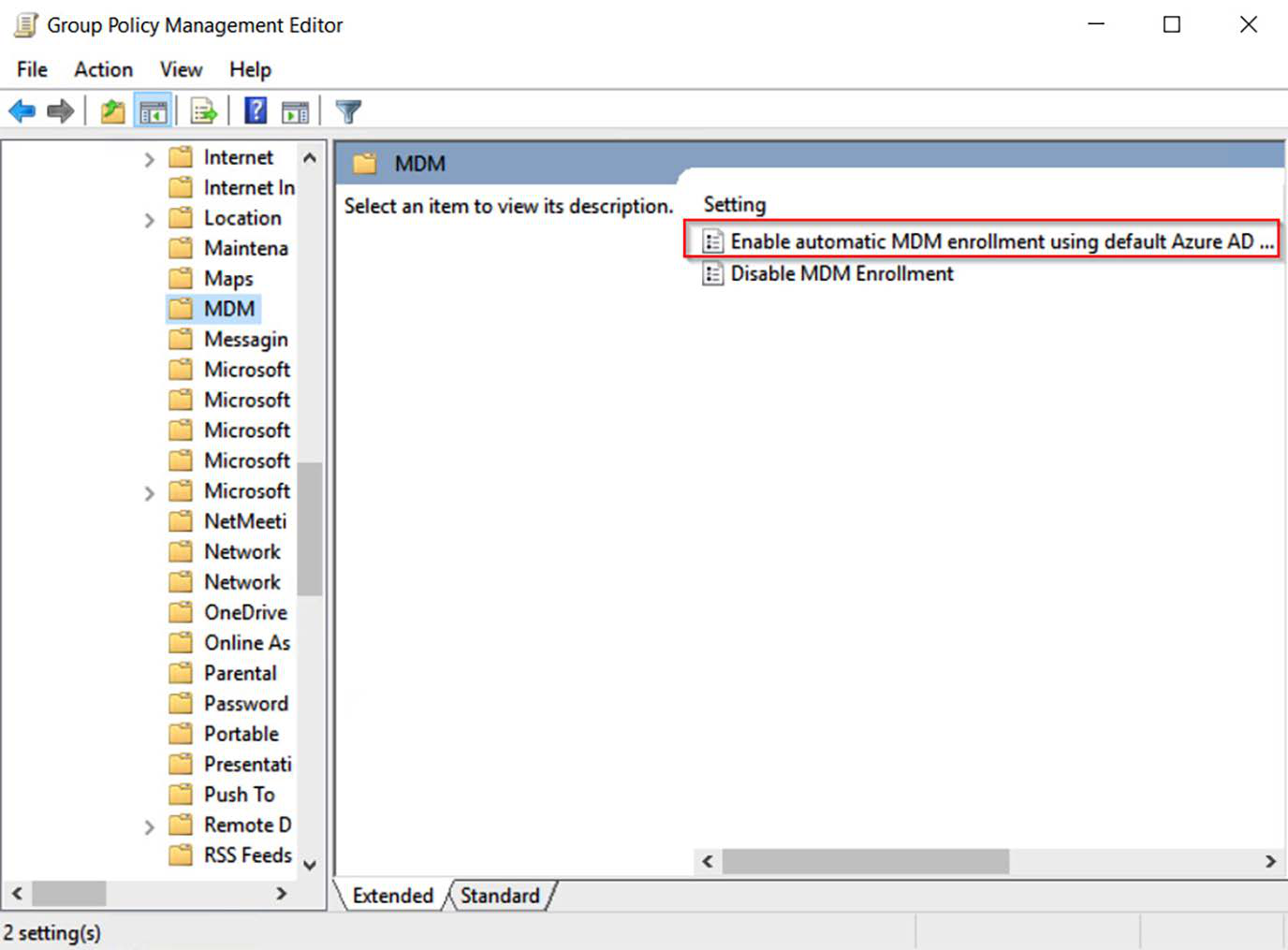
Let’s get started configuring the GPO that configures automatic MDM enrolment for Hybrid Entra joined devices with a device token:
1. Log on to your session host.
2. Open Local Computer Policy and click Administrative Templates | Windows Components | MDM:


Comments
Post a Comment