Amazon Cognito user pools
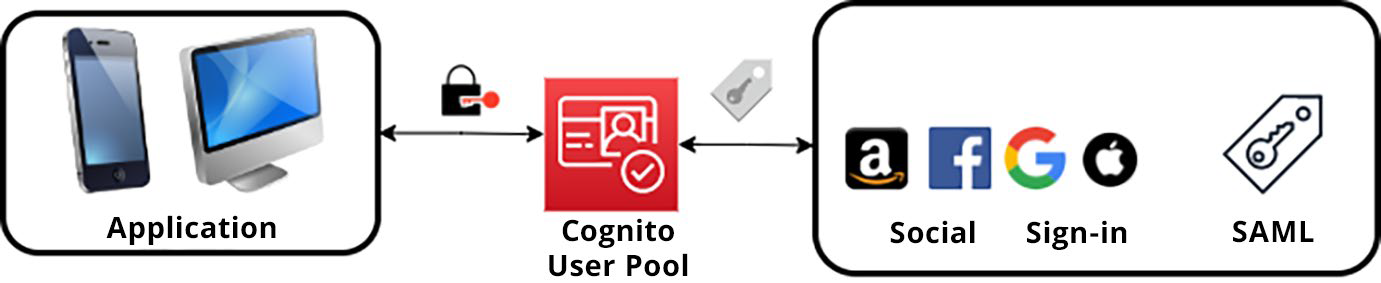
Amazon Cognito user pools are one of two primary components of Amazon Cognito. They allow you to create and manage user identities, handle user registration and sign-in, and securely authenticate users. With user pools, you can set up customizable sign-up and sign-in pages for your applications, support different authentication methods (such as linking username/password, social login, or corporate identities), and manage user profile information. They also offer security features such as MFA and integration with AWS services. Furthermore, user pools take care of user registration, authentication, and profile management, making it easier for developers to handle user accounts and security in their applications without reinventing the wheel. Once a user is authenticated via the user pool, either from the user pool itself or via a third-party IdP, Amazon Cognito will generate tokens that manage the access to your cloud-based or mo...
